From Siloed Subsidiaries to Connect Risk Insights with Resilience ARC.
ARC helps CISOs and CROs assess subsidiary company risk, spot common gaps, and drive enterprise-wide mitigation, turning static due diligence into continuous oversight with integrated insurance intelligence and insights from the Risk Operations Center.
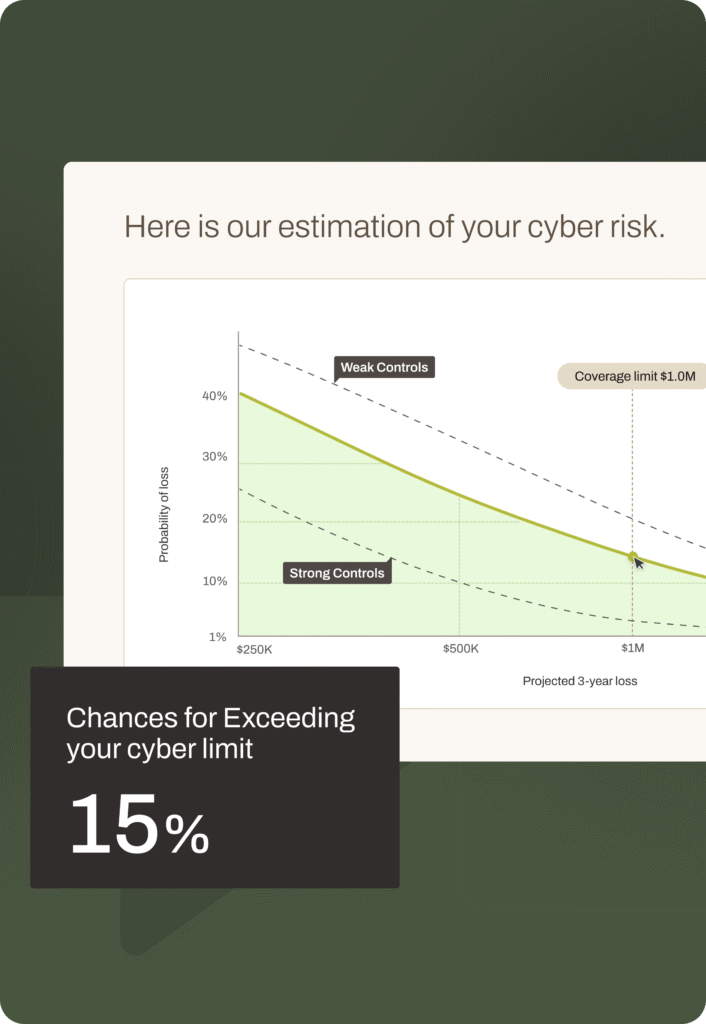
Cyber risk poses a huge challenge for subsidaries and holding companies.
Inconsistent Visibility Drives Unmanaged Exposure
Without standardized visibility into subsidiary-level risks, critical exposures remain hidden—leading to compliance failures, higher incident costs, and inefficient use of cybersecurity budgets.
Fragmented Views Undermines Risk Planning
When cyber risk can’t be rolled up or attributed across the portfolio, leaders struggle to prioritize investments, quantify exposure, or defend spend to boards and insurers—stalling risk-informed decision-making.
Operational Gaps Erode Cyber Resilience at Scale
Managing cyber risk across non-integrated, decentralized entities increases friction, delays remediation, and inflates program costs—ultimately weakening enterprise-wide cyber resilience.
Make Better Cyber Business Decisions
with Resilience ARC.
Standardized Risk Visibility Across Subsidiaries
Establish a shared risk language, eliminates blind spots, and enables proactive risk management across the entire organization.
Aggregate and Attribute Risk at the Portfolio Level
Give business unit leadership the clarity to prioritize, justify, and defend cyber risk investments with confidence.
Maintain Risk Oversight and Deliver Economies of Scale
Drive consistent execution across subsidiaries, reduce duplication of effort, and lower overall program costs to deliver scalable risk management with clear accountability and faster responses.
Manage cybersecurity due diligence across your portfolio with Threatonomics™
Cyber Risk Profile Capture
Collect the current state of cybersecurity controls at each portfolio company to establish a foundational risk profile.
Breach & Attack Simulation
Run simulations to assess baseline control effectiveness against real-world adversary tactics, enabling tailored risk insights and prioritization.
Findings & Exposures Monitoring
Leverage a mix of external threat intelligence, including dark web monitoring and domain scanning, to surface exposures. Critical threats are escalated by the Risk Operations Center (ROC) as actionable findings.
Compliance Validation (NIST & DORA)
Validate cybersecurity posture against regulatory frameworks like NIST and DORA using evidence from breach and attack simulation results and identified control gaps.