Safeguard Value from Acquisition to Exit
ARC helps CISOs and CROs assess portfolio company risk, spot common gaps, and drive enterprise-wide mitigation, turning static due diligence into continuous oversight with integrated insurance intelligence and insights from the Risk Operations Center.
Private Equity acquired assets possess a higher risk of cyber attack.
From Announce to Close
68% of clients see an uptick in cyber incidents during the month of a deal closure.
Post Closing Risk
For clients who see an uptick, the increase in incidents can spike as high as 116% the month after deal closure showing that the acquired company—and the acquirer—face a period of increased cyber risk after a deal is struck.
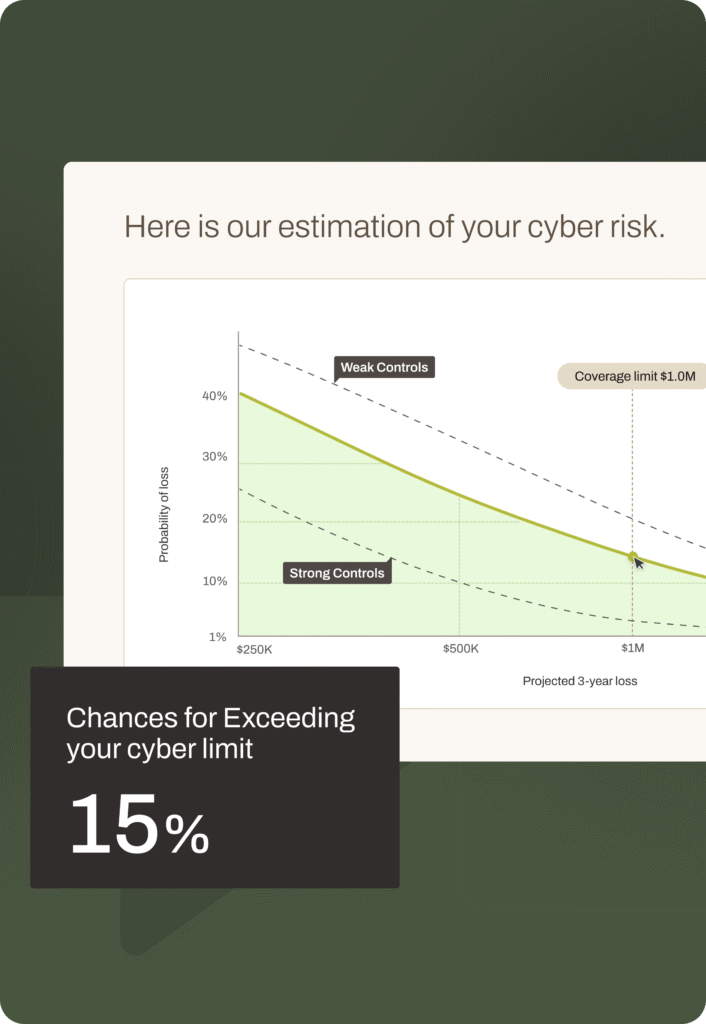
Impact to PE Firms
The average ransom paid by mid-sized companies topped $1MM+ in addition to potential downstream impacts such as rising insurance costs or loss of customer trust.
ARC empowers Private Equity firms to manage cyber risk across the entire portfolio.
Portfolio Company Onboarding
Onboard and manage each portfolio company in the Threatonomics™ platform to standardize cybersecurity due diligence and gain a unified, real-time view across your entire portfolio.
Unified View of Cybersecurity Controls
Continuously review and deliver aggregated portfolio risk and gap reports to portfolio managers.
Incident Response Planning
Prepare for and test incident response scenarios, including duided Incident Response Planning Workshops and Tabletop Exercises.
Prioritized Security Roadmap
Reduce financial risk with our portfolio Cyber Action Plan, which prioritizes next-best cybersecurity actions based on their impact and cost.
Manage cybersecurity due diligence across your portfolio with Threatonomics™
Cyber Risk Profile Capture
Collect the current state of cybersecurity controls at each portfolio company to establish a foundational risk profile.
Breach & Attack Simulation
Run simulations to assess baseline control effectiveness against real-world adversary tactics, enabling tailored risk insights and prioritization.
Findings & Exposures Monitoring
Leverage a mix of external threat intelligence, including dark web monitoring and domain scanning, to surface exposures. Critical threats are escalated by the Risk Operations Center (ROC) as actionable findings.
Compliance Validation (NIST & DORA)
Validate cybersecurity posture against regulatory frameworks like NIST and DORA using evidence from breach and attack simulation results and identified control gaps.