Executive Summary
Kimsuky is a North Korean APT group tasked with global intelligence collection operations aligned with the North Korean government’s interests. The group has been active since at least 2012 and has a particular interest in South Korean think tanks and government entities; however, it also targets the United States, the United Kingdom, and other European countries. Kimsuky specializes in targeted phishing campaigns, leveraging malicious attachments in follow-on emails after establishing trust through email correspondence [1][2].
In the Spring of 2024, the NSA and FBI released a joint cybersecurity advisory pointing to the Democratic People’s Republic of Korea (DPRK, a.k.a. North Korea), specifically Kimsuky exploiting improperly configured DNS Domain-based Message Authentication, Reporting and Conformance (DMARC) record policies to conceal social engineering attempts [3]. This advisory characterized DPRK’s tendency to pose as academics, journalists, or other East Asian experts for campaigns against South Korea, the United States, and Europe [2][3].
In late July 2024, Resilience analysts observed an Operational Security (OPSEC) mistake made by threat actors assessed to be Kimsuky. Our analysts took advantage of this to collect a trove of source code, login credentials, traffic logs, and internal notes. From the data we collected, we assess that Kimsuky is phishing University staff, researchers, and professors to conduct espionage. Once inside University networks, Kimsuky can pilfer research and intelligence for the North Korean government.
These actions align with the goals of the Reconnaissance General Bureau (RGB), which is the primary foreign intelligence-gathering organization of the North Korean government. Kimsuky has previously attempted to steal nuclear weapons research, healthcare, and pharmaceutical secrets [4]. In some instances, Kimsuky has also been identified as conducting financially motivated cybercrime, believed to be funding their espionage activities [4]. North Korea seeks to use this information to improve its country, which severely lacks an established scientific community.
The technical details and recommendations below provide additional information on how Kimsuky operates and targets Universities to further North Korean espionage operations.
Resilience Recommendations
Resilience recommends the following high-level strategies for persons who may be the target of a state-backed campaign:
- Leverage phish-resistant Multi-factor authentication such as FIDO-compliant hardware tokens or push-based mobile applications.
- Always double-check that the URL you are logging into matches the page you expect to be logged into. Some password managers will do this automatically.
- Review and test the Breach and Attack Simulation packages that simulate Kimsuky activity.
Technical Details
Staging Infrastructure
Previous reports from CISA indicate that Kimsuky uses compromised internet hosts to stage their attacks. From the data we collected, they had access to audko[.]store, dorray[.]site, nusiu[.]live, osihi[.]store, simos[.]online, sorsi[.]online, wodos[.]online, and wodods[.]xyz.
After gaining access to infrastructure to conduct their attacks, the threat group staged a webshell called “Green Dinosaur” on the host. This webshell allows operators to upload, download, rename, and delete files. This webshell appears to be based on code taken from an old webshell called Indrajith Mini Shell 2.0 [5]. Green Dinosaur, however, removed functionality in a way that limits detection possibilities while allowing the features for operators to put phishing websites into place.
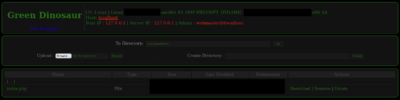
Image: “Green Dinosaur” webshell
The GreenDinosaur samples we obtained from Kimsuky’s infrastructure are all obfuscated with multiple layers of base64 and gz deflated strings, likely to prevent detection by hosting companies. The final layer was a mixture of base64 and multi-character substitution using the PHP function `strtr`.
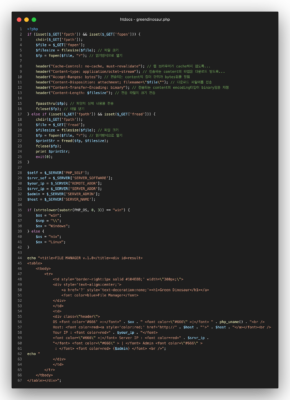
Image: Deobfuscated “Green Dinosaur” webshell source code sample
Phishing Pages
After setting up Green Dinosaur, the operators upload prebuilt phishing pages. These phishing pages are created by first scraping the real login portals they are imitating. The scraped page is then modified with additional code to log any entered credentials. In this campaign phishing pages were created for Dongduk University, Korea University, and Yonsei University. Additionally, we discovered a phishing toolkit for stealing Naver accounts.
Dongduk University
The Dongduk University phishing page is visually identical to the real Dongduk email login page but contains modifications to weaponize it.
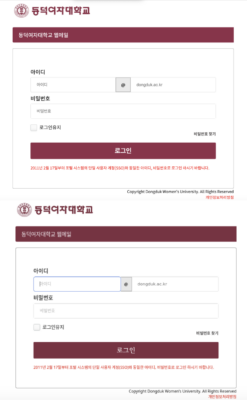
Image: Legitimate Dongduk login page (Top) and the Kimsuky malicious login page (Bottom) show stark similarities.
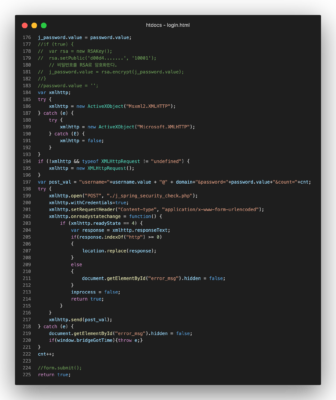
Image: Screenshot of the modified Dongduk login page HTML code
The code above is the main piece added to the login page. The developers first commented out the sites default behavior of encrypting the passwords value with Dongduks public RSA key. The following code takes the username, password, and number of login attempts and sends it to j_spring_securty_check.php instead of using the normal submission function. This PHP file contains the following code:
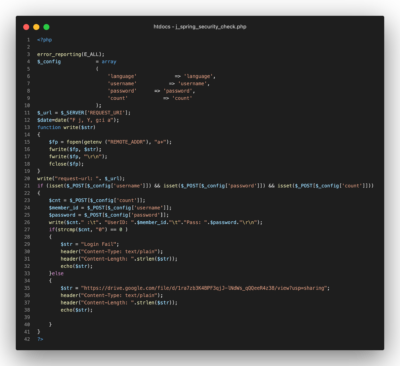
Image: Screenshot of the j_spring_security_check.php code
This file has nothing to do with j-spring or security, it collects information about the visitor, the current time, and logs the victims username and password to a file on the server. From the victims perspective, after their first attempt to login, they see a message that says “Login Fail” and are prompted to enter their credentials again. This is likely to ensure the threat actors obtained a password without typos. After the second attempt they are redirected to another site as if the login worked correctly but really their credentials are merely being logged to a text file on the server.
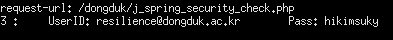
Image: Screenshot of credentials being logged
For the targets at Dongduk University they are redirected to a PDF titled “2024년 8월 비공개 아산정책포럼 참석요청서 계획(안)” (Translation: The August 2024 private Ansan Policy Forum plan (draft)) hosted on Google Drive (https[://]drive[.]google[.]com/file/d/1ra7zb3K4BPF3qjJ-lNdWs_qQQeeR4z38/view). On Google Drive this pdf was uploaded by kimduyong2020@gmail[.]com, a Google User with a profile photo of the South-North Korea Exchanges and Cooperation Support Association.
![Image: South-North Korea Exchanges and Cooperation Support Association Logo used as a profile photo for kimduyong2020@gmail[.]com](https://cyberresilience.com/wp-content/uploads/2024/08/ico_app1-400x400.png)
Image: South-North Korea Exchanges and Cooperation Support Association Logo used as a profile photo for kimduyong2020@gmail[.]com
The PDF is an invitation to the Asan Institute for Policy Studies August Forum. This lure is potentially the same mentioned in a blog post by the real Asan Institute on July 16, 2024 warning members of phishing attacks from Daum, Gmail, and Naver accounts [6].

Image: The Asan Institute for Policy Studies August Forum PDF
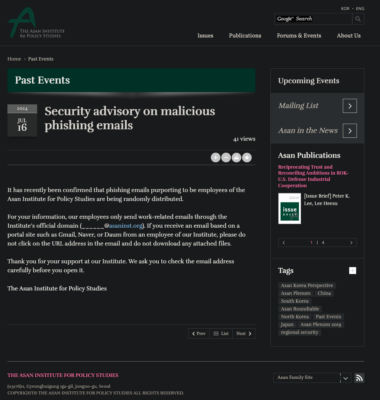
Image: The Asan Institute for Policy Studies- Past Events: ‘Security advisory on malicious phishing emails’
Korea University
The Korea University login page takes a similar approach to Dongduk but instead of modifying the HTML of the document, instead one of the javascript imports is modified to pass off the login credentials.
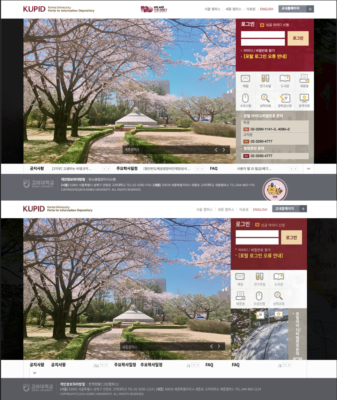
Image: the legitmate Korea University login page (Top) and Kimsuky’s malicious login page (Bottom) show stark similarities.
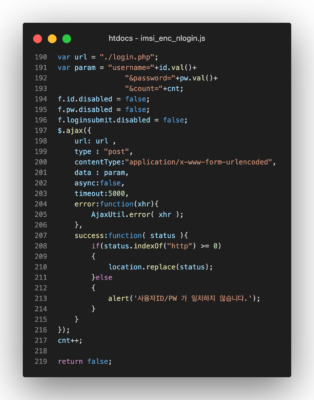
Image: Screenshot of the modified Korea University javascript code
The login.php file that the urlencoded username, password, and count are sent to is identical to the j_spring_securty_check.php file found on the Dongduk phishing page but instead redirects victims to the real login page at https://portal.korea.ac.kr/mail/.
Yonsei University
The Yonsei University login page takes an almost identical approach to Dongduk and uses AJAX to transmit the credentials to login.php.

Image: Legitimate Yonsei University login page (Top) and the Kimsuky malicious login page (Bottom) show stark similarities.
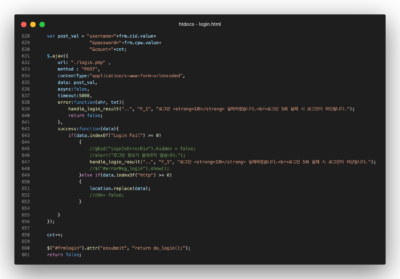
Image: Screenshot of the modified Yonsei login page HTML code
The login.php file that the urlencoded username, password, and count are sent to is identical to the j_spring_securty_check.php file found on the Dongduk phishing page but instead redirects victims to the real login page at https://mail.yonsei.ac.kr/.
Naver
Additionally on Kimsuky’s phishing sites, there is a non-target specific phishing toolkit to gather Naver accounts. This toolkit is a rudimentary proxy akin to Evilginx for stealing cookies and credentials from visitors and shows popups telling users they need to login again because communication with the server was disrupted.
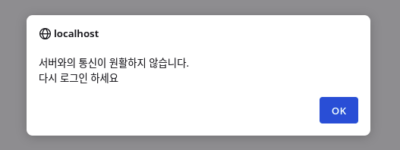
Image: Screenshot of Kimsuky’s malicious popup telling user to login again due to server communication error
After clicking ok on the popup, the victim is redirected to a fake Naver login page.
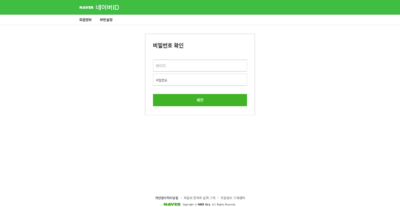
Image: Screenshot of Kimsuky’s malicious Naver login page
SendMail
To get targets to visit these phishing sites, Kimsuky uploaded a custom PHPMailer implementation using GreenDinosaur simply called “SendMail”. For the campaign we observed, this PHPMailer utilized the compromised email account of a professor at Seoul National University to access a SMTP server hosted in South Korea for the CRM app Dooray. In SendMail, multiple gmail and daum accounts were also used as source addresses. In a text file of notes written by the operators, several gmail and daum accounts were listed with their password, recovery email, and 2fa backup codes. These email accounts were used to send phishing emails to employees of Dongduk University, Korea University, Yonsei University, and other targets. Links in the notes also point to the “send” tool being hosted at “http://penlu[.]or[.]kr/data/view[.]php” at some point. All of the email accounts we discovered had the same password “1qaz2wsx#EDC$RFV” and the same recovery email: “nasndaoop@gmail[.]com”.
Phishing Accounts
nahoiu95@gmail[.]com
nolpoaw@daum[.]net
nasaioy0@gmail[.]com
nboipw@daum[.]net
nkodfgl@gmail[.]com
naokilw@daum[.]net
nsmnop99@gmail[.]com
nabsoiu@daum[.]net
nanmskeo@gmail[.]com
nmakope@daum[.]net
nasndaoop@gmail[.]com
aaa@naver[.]com
no-reply@sisileae[.]com
The configuration for SendMail we obtained was preloaded for multiple Naver themed phishing email with the subject line “네이버 아이디 탈퇴가 완료되었습니다”(Translation: Naver ID was successfully deleted) and “[네이버]메일 송수신 기능 제한 알림.” (Translation: There are restrictions with sending and receiving Naver mail.) These and other phishing emails linked back to numerous phishing sites.

Image: Screenshot of Kimsuky’s SendMail tool
Indicators of Compromise
You can find our IOCs for Kimsuky on our GitHub.
Citations
[1]https://www.cisa.gov/news-events/cybersecurity-advisories/aa20-301a
[2]https://media.defense.gov/2023/Jun/01/2003234055/-1/-1/0/JOINT_CSA_DPRK_SOCIAL_ENGINEERING.PDF
[3]https://www.ic3.gov/Media/News/2024/240502.pdf
[4]]https://services.google.com/fh/files/misc/apt43-report-en.pdf
[5]https://packetstormsecurity.com/files/119233/Indrajith-Mini-Shell-2.0.html
[6]https://en.asaninst.org/contents/security-advisory-on-malicious-phishing-emails/


