
With an astonishing 95% of cybersecurity breaches attributed to human error, organizations must educate, train, and implement a security foundation for all employees. This staggering statistic highlights the vulnerability of humans within digital infrastructures and underscores the importance of building a security-forward mindset into the culture of resilient businesses.
As cyber threats continue to lead to breaches, shifting from traditional cyber risk management to a holistic emphasis on Cyber Resilience is becoming a crucial strategic pivot. Adopting a new approach to tackling cybersecurity threats necessitates moving beyond mere prevention to build an adaptable and robust defense mechanism.
Cyber risk experts are dissecting this transition’s complexities to uncover effective strategies. These strategies aim to enhance the tactical security tools and the resilience-promoting mindsets and behaviors within a business. Five key principles form the fundamental building blocks of this strategy.
5 Principles of Cyber Resilience to Strengthen the Core of Cybersecurity
As organizations evolve from traditional cyber risk management to a more holistic approach to managing their risk, understanding and implementing our principles of Cyber Resilience becomes crucial. These principles provide a framework for organizations to defend against cyber threats and thrive despite them.
These foundational principles underpin a revolutionary cyber resilience strategy, guiding organizations in their quest to safeguard their digital assets while ensuring business continuity.
1. Tolerates Losses Within Limits
Cyber resilience acknowledges the inevitability of cyber threats. It prioritizes building an organization’s ability to absorb acceptable losses while minimizing damage and bouncing back quickly. Key decision-makers like the CFO, CRO, and CISO collaborate to define your risk tolerance. Considering the potential financial impact of cyber incidents is crucial to ensuring your organization has the resources to withstand them.
Cyber insurance acts as a financial safety net, covering losses exceeding your defined tolerance level. The insurance limit outlines the maximum payout. However, robust risk management goes beyond insurance. It also involves ensuring sufficient capital reserves to handle unexpected losses outside the scope of coverage.
The CFO plays a crucial role by managing financial resources and ensuring they can absorb these potential hits. You can build a stronger cyber resilience strategy by understanding your acceptable loss level and having adequate financial buffers.
2. Connect Security and Risk Transfer
Security investments mitigate risk by reducing the likelihood of experiencing a material loss. Once you have actually incurred a material loss, insurance kicks in.
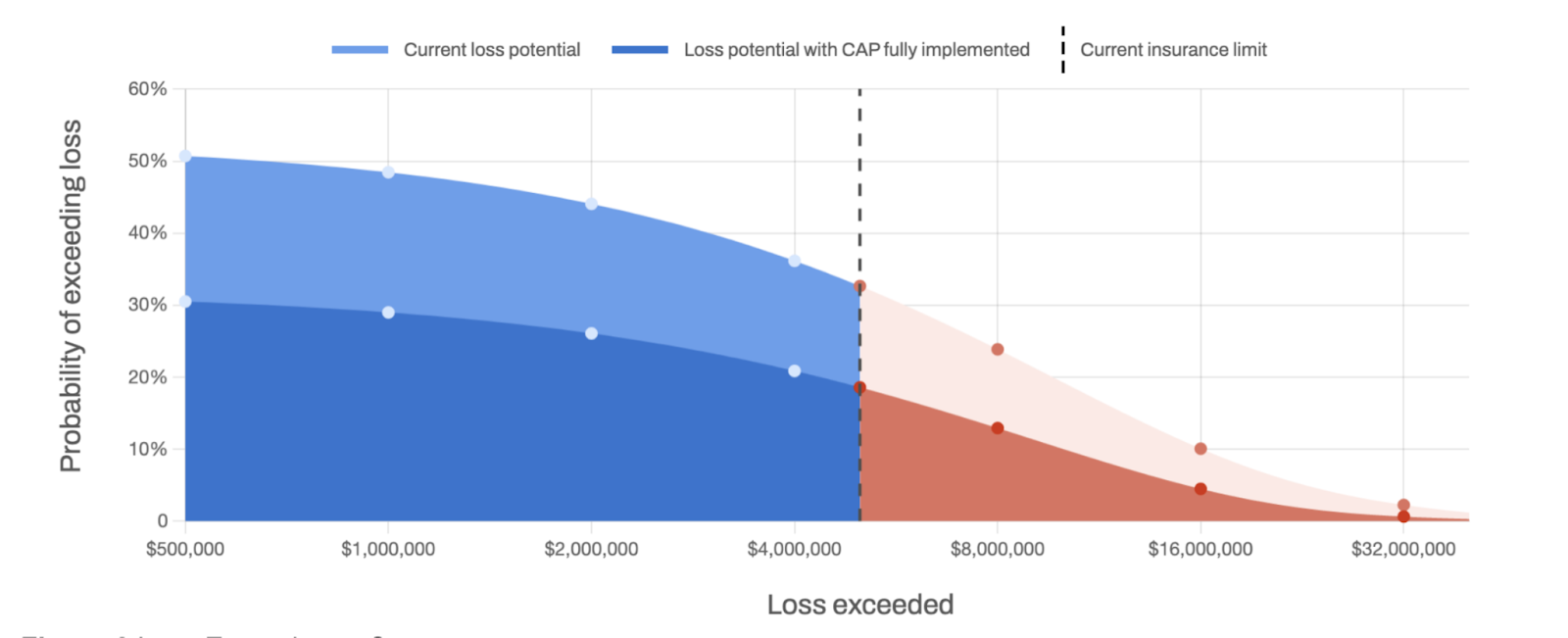
Think of security as a downward motion while transfer moves the limit from left to right. In the image above, the limit is the dotted line on the x-axis at about $5 million.
Mitigation and transfer, in effect, work like the dials on an etch-a-sketch to bring risk within tolerance. Here is the challenge: getting the transfer you want largely depends on the state of your security controls. If your controls need to be stronger relative to assessing risk, you will have trouble getting the level (and price) of insurance you want. You may not be able to get insurance at all.
Given the complexities of this challenge, we should not consider security controls independently of fund transfers or the protection of capital reserves. The CISO, CFO, and CRO must work together through a shared “Cyber Resilient Objective,” with a quantitative goal of keeping risk within tolerance.
3. Seek Capital Efficiency but Prevent Negligence
Cyber resilience prioritizes capital efficiency without compromising security. Investing too heavily in security can hinder growth, while underinvestment leaves you exposed to crippling losses. The key lies in optimizing your security spend.
Return on Controls (ROC) prioritizes security measures based on their cost-effectiveness in reducing the likelihood of losses. By mitigating the most probable and damaging threats, you ensure that your security budget is maximized. Our strategy prevents negligence by minimizing potential material losses at the lowest possible cost.
After implementing security controls, insurance steps in to cover any residual risk that exceeds your tolerance level. The CFO plays a crucial role in setting this limit to minimize the impact on financial reserves. This remaining, potentially high-impact risk (often called “tail risk”) is managed through a combination of mitigation, insurance, and adjustments to capital reserves. The optimal balance between these three elements minimizes both cost and potential damage.
4. Make Risk Surface Visible and Manageable
Imagine your organization’s cyber risk profile as a “cyber resilience risk surface.” This surface considers the potential losses from various cyber threats. By mapping and quantifying this relationship, you can assess your company’s value-at-risk – the potential financial impact of cyber incidents.
Security controls shrink this surface by reducing the likelihood of attacks, while risk transfer (insurance) lessens the impact of successful attacks. Finally, capital reserves act as a backstop for losses exceeding insurance coverage. Monitoring this risk surface allows you to proactively identify changes that might push your risk profile outside your tolerance level.
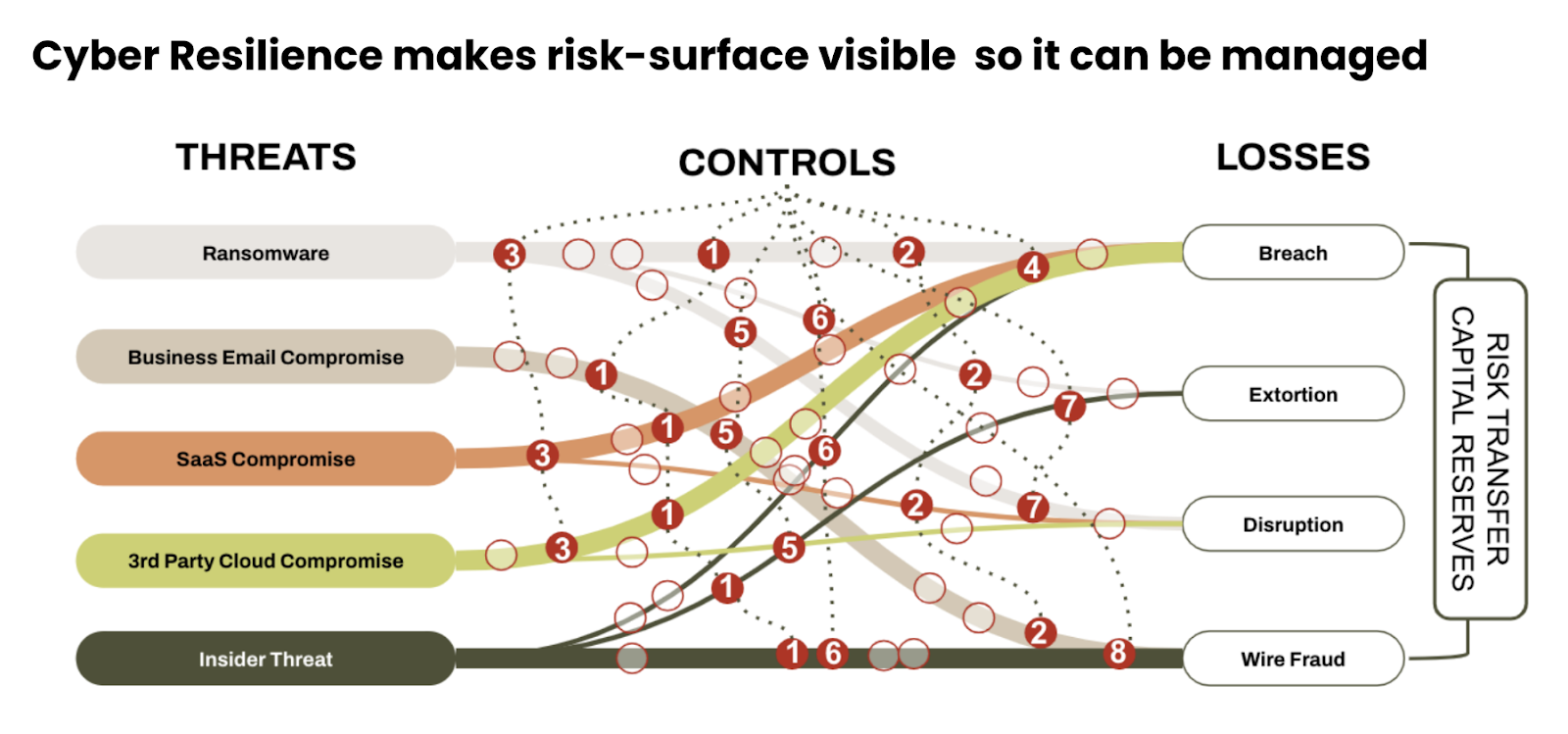
Similar to traditional threat intelligence, monitoring the risk surface involves keeping track of emerging threats like zero-day exploits or state-sponsored attacks. However, cyber resilience goes beyond just identifying threats. By analyzing how these threats impact your value-at-risk, you can proactively adjust your security controls, insurance limits, or capital reserves to maintain a balanced and efficient cyber resilience strategy. This ensures you’re not just identifying threats, but also managing their potential financial consequences.
5. Promote Strong Cyber Hygiene by Maximizing Return on Controls (Roc)
Cyber resilience incentivizes good cyber hygiene practices by focusing on maximizing return on investment (ROI). This means prioritizing security controls that address the most significant threats (material risk) while aligning with industry standards.
Using the Return on Controls (ROC) approach, controls are ranked based on their efficiency in reducing losses. High-ROI controls minimize the most damage at the lowest cost. Maximizing ROC allows you to implement more controls across a wider range of risks, ultimately leading to a more comprehensive and better risk posture.
The most effective security measures often have a broad impact, addressing multiple threats simultaneously. A prime example is a ‘zero trust architecture’ initiative, which includes measures like multi-factor authentication (MFA) and privileged access management (PAM). This strategic approach can significantly reduce material risk relative to its cost, making it a high-priority investment. Other measures are then prioritized based on their calculated ROI.
Redefining the Approach to Cybersecurity
Historically, the foundation of cybersecurity strategies has been cyber risk management, which involves identifying, defending, and managing an organization’s value-at-risk. The increasing sophistication and frequency of cyber threats have made it evident that not all risks can be eliminated entirely. Instead, organizations must identify the value that they must defend with security, transfer with insurance, and potentially accept as they focus investments in the most relevant areas.
This is a key component to the strategy of Cyber Resilience – tolerating cyber losses within limits, and defending what is most important for the organization to continue to deliver value. Cyber Resilience adopts a holistic approach to cybersecurity, cyber insurance, risk quantification, and overall cyber risk management. When we are too close to the problem it can be hard to see.
It is easy to focus on unnecessary tactical activities such as frameworks, standards, or controls. Resilience helps to align focus on what is a priority and delivers the most ROI. This ensures businesses can withstand an incident / attack and minimize losses while continuing to deliver value. We call this new approach of value-driven risk management, Cyber Resilience.
Quantifying Cyber Risks: Establishing a Cyber Resilience Foundation
Cyber risk quantification within a resilience framework is a multi-dimensional approach that involves a deep dive into evaluating the potential financial impact of cyber threats. By quantifying risks in terms of dollars and cents, organizations can gain a clearer perspective on the severity and potential damage of different cyber threats, guiding strategic decision-making in cybersecurity investments and policy development.
Quantifying risk is an intricate process that requires a comprehensive understanding of an organization’s digital assets – or value at risk, the various threats posed to these assets, and the potential financial repercussions of these threats materializing. This involves data analysis, threat modeling, and collaboration across departments to gather insights into potential vulnerabilities and their impacts. It’s a dynamic process that adapts as new threats emerge and the organization’s digital footprint evolves.
Integrating Security and Insurance Considerations
Integrating security and insurance considerations into your cyber risk management strategy is a pivotal aspect of risk quantification. Organizations can evaluate the cost-effectiveness of different risk transfer mechanisms, such as cyber insurance, by understanding the financial impact of potential incidents. Cyber insurance plays a vital role in the Resilience strategy by offering a means to manage residual risk that exceeds the organization’s risk acceptance threshold. This not only provides a financial safety net in the event of a breach but also encourages the adoption of best practices in cybersecurity risk management as part of the insurance underwriting process.
Ultimately, quantifying risks enables a balanced approach to cyber defense, where organizations can navigate the trade-offs between investing in preventive measures and accepting certain levels of risk. This balanced approach is crucial for building a strong security posture that aligns with the organization’s overall business strategy and objectives. It ensures that cybersecurity efforts are not just about deploying the latest technologies but about making strategic investments that contribute to the long-term success of the organization.
Establishing KRIs (Key Risk Indicators) in Cybersecurity
In cybersecurity, threats evolve with alarming speed and complexity. Establishing Key Risk Indicators (KRIs) is a critical strategy to monitor and manage potential vulnerabilities before they escalate into full-blown security incidents, embedding an early warning system within the cybersecurity framework.
KRIs are specific, quantifiable measures that are selected for their ability to provide an early signal of increasing risk exposure in various areas of organizational operations. In cybersecurity, these indicators could range from the number of unsuccessful login attempts to detect potential unauthorized access to the detection rate of malware by security systems, signaling the effectiveness of preventive measures in place.
The selection of KRIs is a strategic process that should align with the organization’s overall risk appetite and cybersecurity objectives. It involves:
- Identifying Critical Assets and Signals: Recognizing what data, systems, or processes are vital to the organization’s operations and could be potential targets for cyber threats.
- Assessing Threat Landscape: Understanding the specific threats that the organization faces can help tailor the KRIs to monitor risks that are most relevant.
- Setting Thresholds: Establishing baseline values for each KRI that trigger alerts when exceeded, indicating a potential or emerging risk that requires attention.
Integrating KRIs into Cybersecurity Strategy
Integrating KRIs into the broader cybersecurity strategy enhances an organization’s ability to identify and address risks preemptively. This integration involves:
- Regular Monitoring: Continuously tracking KRIs to detect deviations from normal patterns that could indicate emerging threats.
- Response Planning: Develop action plans that can be activated when KRI thresholds are breached, ensuring that potential risks are mitigated swiftly and efficiently.
- Continuous Review and Adaptation: Regularly reviewing and updating KRIs to reflect the evolving cyber threat landscape and the organization’s changing risk profile.
The inclusion of KRIs in the cybersecurity arsenal is not just about monitoring and detection; it’s about fostering a culture of resilience where organizations are prepared to respond to threats and constantly adapt their defenses in anticipation of future risks. This strategic emphasis on KRIs paves the way for a more secure and resilient organizational future, where cybersecurity is not just reactive but anticipatory and adaptive.
With Cyber Resilience solution, you get expert-triaged threat alerts personalized and prioritized for individual business attributes. You receive alerts to industry-specific threats, threat actor campaigns, active ransomware groups, trending malware, and vulnerabilities under active exploit, all validated by our security and risk experts to reduce false positives and redundancies.
Merging Financial and Insurance Insights with Cybersecurity
Advancing beyond conventional security measures requires thoroughly integrating financial and insurance insights into cybersecurity strategies. This perspective views cybersecurity not only as a technical challenge but also as a financial one, where the costs associated with potential breaches are balanced against the investments in protective measures.
By adopting this financial viewpoint, organizations can develop security budgeting strategies that reflect the true costs associated with cyber risks and the value of resilience. Cyber insurance is a vital component in this context, offering a means to manage residual risk that cannot be mitigated through security measures alone.
Addressing Challenges with Strategic Practices
Adapting to a focus on Cyber Resilience necessitates advanced technology, processes, and a shift in organizational culture. Everyone has a role in recognizing cybersecurity as a collective responsibility and contributing to the organization’s resilience.
Key practices for overcoming these challenges include:
- Thorough Risk Assessments: Conduct comprehensive risk assessments to identify vulnerabilities and prioritize threats based on potential impact.
- Incident Response Preparedness: Developing, testing, and regularly revising an incident response plan detailing the organization’s response to various cyber incidents.
- Adaptive Monitoring and Response: Employing continuous monitoring tools for real-time threat detection and adapting strategies based on evolving threat intelligence.
- Cultivating Awareness and Education: Building a culture of cybersecurity awareness through ongoing training and education for all employees.
Reimagining Cyber Risk Management: A Path to Enhanced Cyber Resilience
The shift from cyber risk management to Cyber Resilience is essential for modern organizations facing the complexities of current cyber threats. By prioritizing a resilient mindset, the culture of an organization can shift from a purely preventative stance to a more sustainable strategy for managing and recovering from cyber incidents.
This strategic realignment enhances our response capabilities to cyber threats. It integrates cybersecurity practices into our broader business strategies, establishing cybersecurity as a pivotal aspect of organizational resilience.
Organizations that adopt this strategic shift will protect their digital assets more effectively and emerge as cybersecurity leaders. The journey from risk management to resilience offers a route to a more secure and adaptable future in cybersecurity. Discover how Resilience can redefine your cybersecurity posture and ensure your organization’s continuity and growth. Request your demo today to see firsthand the transformative power of a cyber resilience-centered approach.






