
This blog post is the first of two supplements to the first webinar of our webinar series “How to Build a Defensible Cybersecurity Budget.”
As a next-generation cyber risk company, our primary goal is to help our clients build resilience against cyber threats. This includes understanding that their risk goes beyond technical challenges. Achieving cyber resilience includes spending money in the wisest ways possible, which means allocating budgeted funds in both a risk-adjusted and risk-tolerant manner. This requires submitting your budget for controls and capabilities in the financial and economic terms of the people who will ultimately approve your budget. These people are the money people— the CFOs and controllers who sign checks— and you must learn to speak their language in a compelling way.
How do these “money people” define a defensible budget? These individuals think about defensible budgets in the following way:
A defensible security budget is a set of allocated costs that serve the strategic objectives of the organization based on a choice of controls that maximizes capital efficiency in an uncertain world.
Allocated costs support actions intended (but not guaranteed) to carry us to a goal. Strategic objectives relate to why an organization exists at all, and capital efficiency relates to the wise and productive use of cash in a risky world.
Combined, this implies that a defensible budget is one that we understand (ironically) to be at risk of failing to achieve its objectives, but not as risky as budgets based solely on technical wish lists and compliance measures alone. No one can ensure that your budget will achieve its goals and objectives, and wishful thinking is not allowed. This is why Resilience has established our cyber risk quantification framework, which allows us to provide a responsible measurement of the risks of failing to achieve the objectives we desire. With that in mind, we can plan proactively to offset and mitigate those risks. The measurement of risk ultimately lives at the heart of a defensible budget to show why it is superior to alternatively motivated requests for a budget.
Identify the Primary Objective: Maximize Shareholder Value
To think like the money people, we first need to think in terms of their objectives. Their primary objective is to maximize shareholder value. This might be controversial in today’s world of focusing on stakeholder value, but shareholders represent a pivotal subset of all stakeholders. Their goals are important enough to function as a filter for any budget approval.
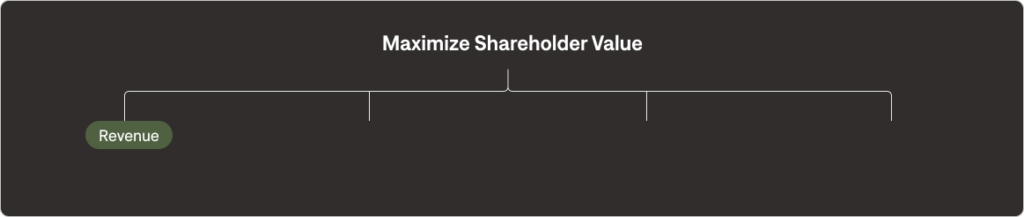
To appeal to the money people’s concerns, we need to ask, “what objectives support maximizing shareholder value?” The easiest suggestion might be simply maximizing revenue.
Revenue is the top line fundamental contributor to shareholder value. It’s the source of contribution to the profit and loss statements from which all other costs are subtracted, and the financial contribution which we hope to retain as much as we can.
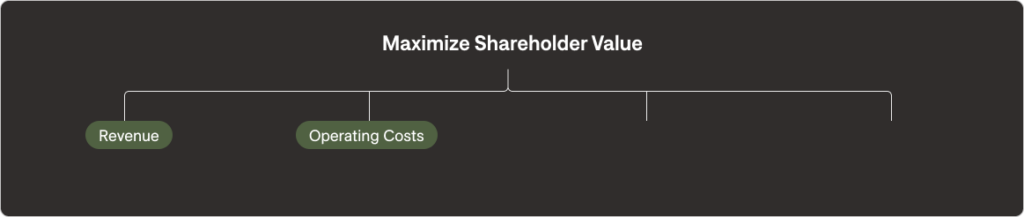
The next fundamental objective to consider is “minimizing operating costs.” Of course, we don’t mean to indiscriminately lower costs, but rather lower the required costs of doing business effectively. We also call this “right-sized costs” or “optimized costs.” Keep in mind that if nothing else changes in the strategic intent of the organization, eliminating waste or unnecessary costs represents a good direction to take.
Taken together, increasing revenue and minimizing operating costs are obvious objectives because they speak to what commercial organizations do: seeking profit. The next two fundamental objectives might seem a little more esoteric, but they are just as important.
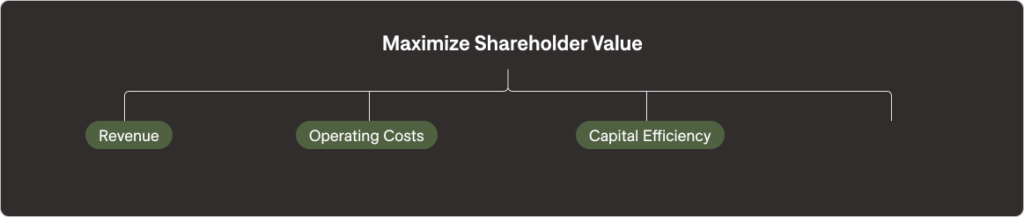
One of these next two key objectives of building a defensible security budget is “maximizing capital efficiency.” What is capital efficiency? It’s related to the wise use of cash, or capital, to accomplish desired outcomes. Sometimes this objective is referred to as maximizing economic profit, and refers to managing investments informed by the risk-adjusted net benefits obtained by the investment. We say capital has been used wisely when we attempt to invest, for example, $100 with the anticipation of eventually making back $150, or $2000. But if we attempt to invest $100 with an anticipated return of less than $100, or even worse, not knowing what the returns might be, then we’re being foolish with the allocation of funds. Money people hate the foolish use of funds.
The last objective we need to pay attention to is the “integrity of the treasury.” The corporate treasury represents the funds that are set aside to support the cash requirements of daily obligations. But it also serves to provide a financial cushion in times of crisis. This cushion, the reserve, is where we draw funds for stormy days. The defensible budget serves to limit the impact to this reserve by handling any realized risks that escape our control.
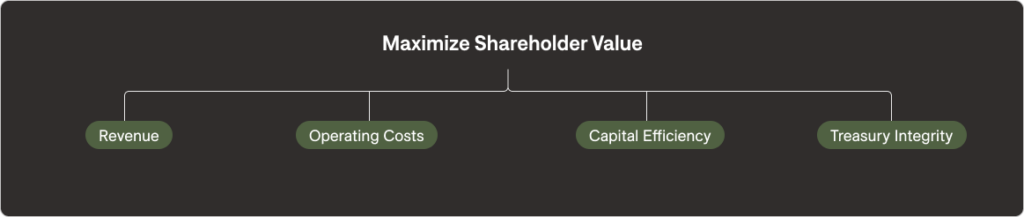
Now that we understand the primary and fundamental objectives of the money people, we need to think about the capabilities we want to achieve through the implementation of controls. Understanding what we want to achieve and the cost of achieving it supports the realization of the four fundamental objectives of building a defensible budget.
For example, we might consider starting with the base capabilities outlined in the NIST Cybersecurity Framework. Given that we start with those capabilities, we need to consider our four objectives and connect the dots for the money people. The goal is to demonstrate a plausible pathway by which these capabilities flow through and support other intermediate business objectives on the way to maximizing shareholder value.
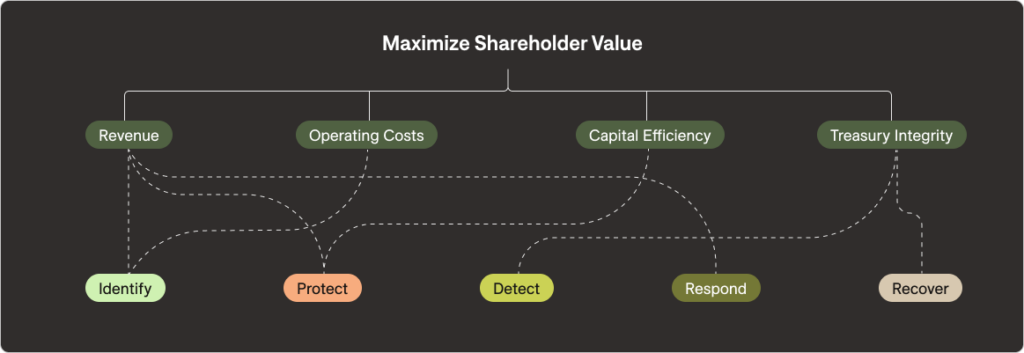
Connect the Dots from Value at Risk to Business Fundamentals
To begin this decomposition of capabilities and objectives, the first step is to understand our Value at Risk. We should ask ourselves, “What is it we stand to lose? What needs to be protected?” If we can answer those questions, then we can brainstorm the capabilities that we need. We then begin a series of iterative questions focused on increasing layers of hierarchically important achievements. What do those capabilities achieve?
Why do we work to achieve threat mitigation? Because it protects the supply chain. Why do we need to protect our supply chain? Because it helps us maintain ongoing business continuity which enables the business purpose.
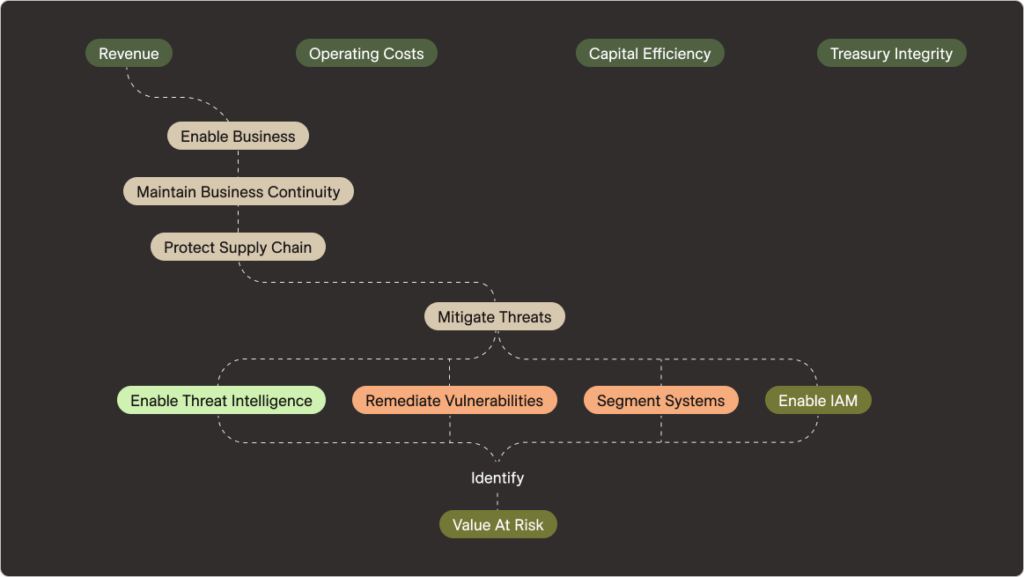
Other goals and pathways can develop from threat mitigation, such as achieving compliance. Why do we want to achieve compliance? Because it enables us to activate the system of trust, without which would preclude us from doing any business at all. In this simple, yet incomplete, decomposition, we’ve clarified for the money people how a subset of capabilities support their fundamental objectives of supporting revenue at a reasonable cost. The remainder of the exercise requires that we connect the dots to capital efficiency and treasury integrity.
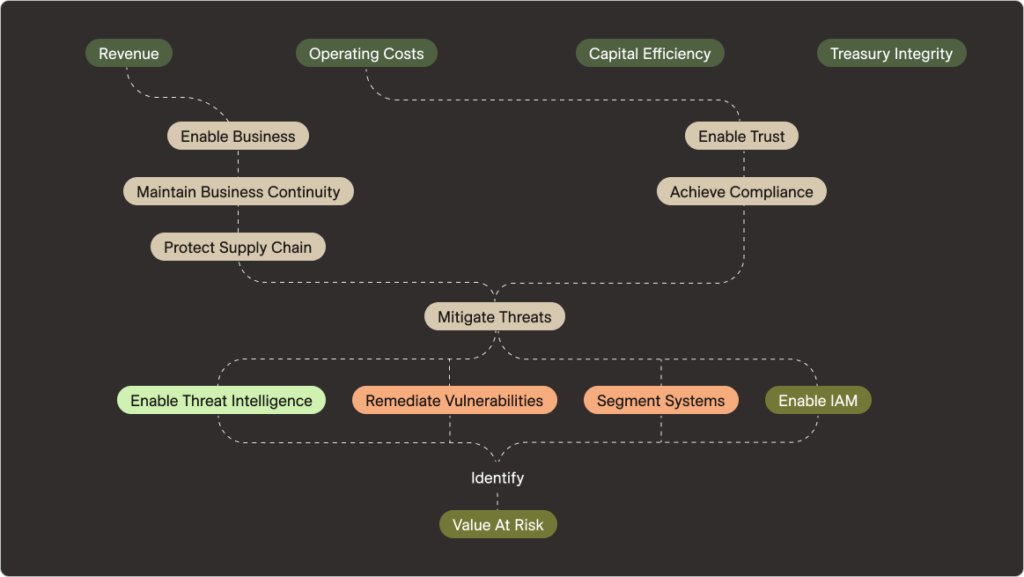
This mapping exercise is very important in helping develop a narrative to defend the quantitative justification for your budget. This provides both you and the money people line of sight from the capabilities you intend to implement or expand to the strategic business objectives they are entrusted to pursue and achieve. Ultimately, clarification across lateral business units helps you enable communication between the finance and security silos that can hamper efforts to build cyber resilience.
To review the full webinar or others within the series follow this link.







