Cyber risk isn’t just evolving—it’s accelerating. And for CISOs and CROs, this shift presents a critical challenge: how to make smarter business decisions that strengthen resilience and reduce material losses. As reported in our 2024 Mid-Year Cyber Risk Report, the past year saw a dramatic shift in how businesses experience and respond to cyber threats, with third-party risks and ransomware driving unprecedented losses. Interconnected systems and external dependencies have created new vulnerabilities, making cyberattacks more far-reaching and costly than ever before.
At Resilience, we tracked these changes across our portfolio, and the data is clear: third-party breaches are no longer just a growing concern—they’re a force in cyber claims. From vendor-targeted ransomware attacks to supply chain disruptions, businesses are facing a new reality in which their security is only as strong as their weakest partner. Meanwhile, ransomware continues to hold its place as the top cause of loss, evolving in both strategy and impact.
For security and risk leaders, navigating this landscape requires a shift in approach. The ability to quantify, mitigate, and transfer cyber risk is now a business imperative. This report highlights key trends that continued from our 2024 midyear report and provides insights into how organizations can align their cyber risk strategies with broader business objectives, ensuring a more resilient and informed path forward.
The rise of third-party risks
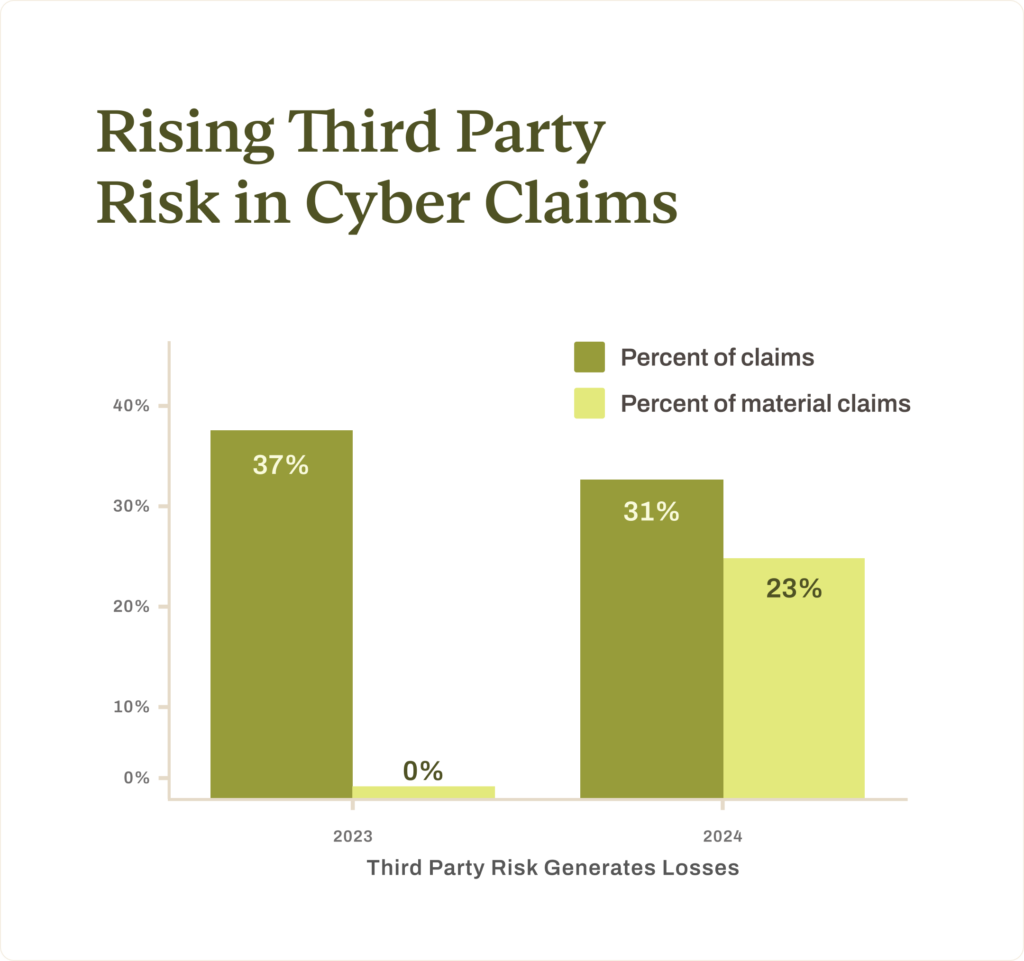
Third-party risks emerged as a dominant driver of cyber claims in 2024, accounting for 31% of all of our client claims. Resilience saw these risks leading to material losses for the first time, making up 23% of material claims. This shift underscores the growing vulnerabilities created by interconnected systems and reliance on external vendors. In 2023, while third party risk was responsible for 37% of claims, none led to incurred losses.
“Third-party risk isn’t only making headlines—it’s driving unprecedented losses. While this risk is often invisible until it’s too late, it’s now clear that the industry has reached a tipping point,” says Vishaal “V8” Hariprasad, Co-Founder and CEO of Resilience. “Businesses can no longer afford to consider their partners’ vulnerabilities as siloed from their own. By understanding this new reality of shared risk, enterprises can make smarter business decisions and meaningfully mitigate material loss.”
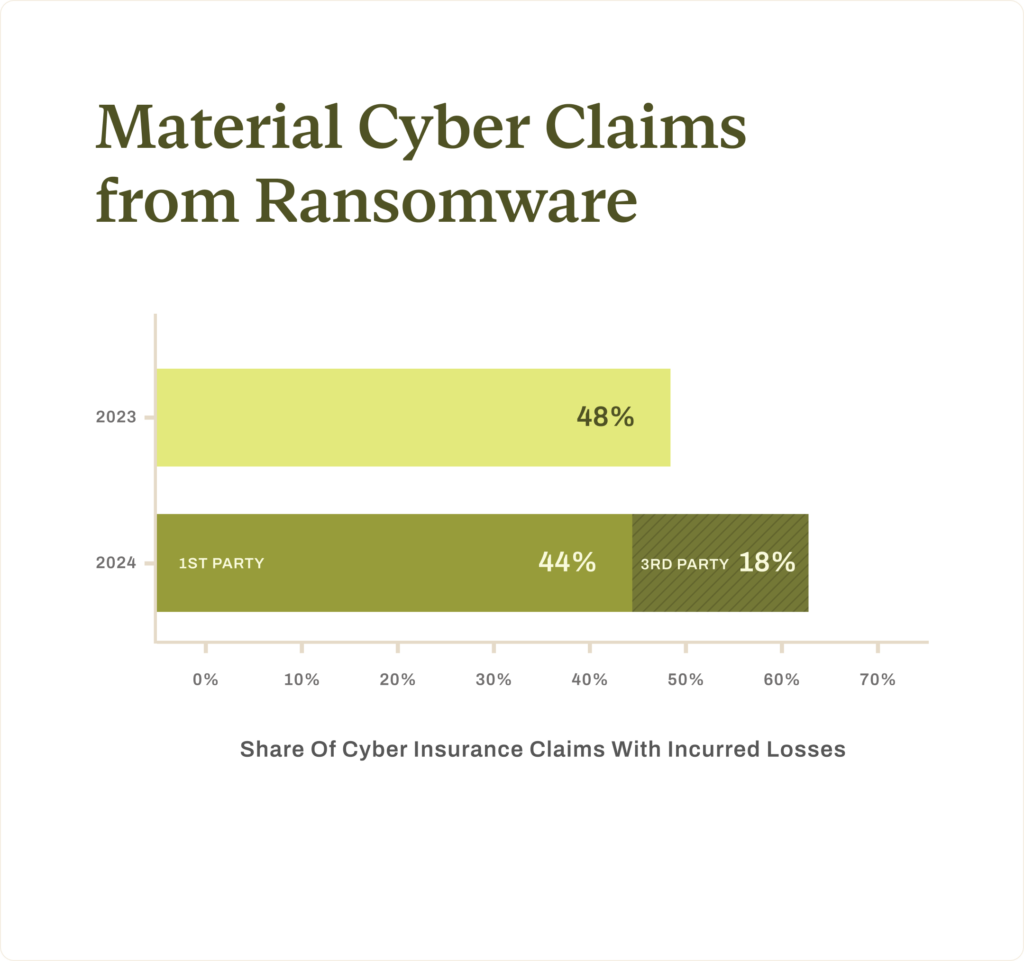
Within the category of third-party risks, ransomware attacks targeting vendors became a significant source of losses, representing 42% of the third-party claim count and accounting for over 100% of actual incurred losses within third-party claims in 2024 at the time of publishing. High-profile incidents such as the breaches at Change Healthcare and CDK Global illustrated how attacks on highly interconnected organizations can ripple across entire industries.
While ransomware has resulted in known losses, not all losses from 2024 are fully developed; claims from the July Crowdstrike outage are expected to result in losses, particularly in cases with significant business interruption. As reported in July, Crowdstrike is one of the safest endpoint detection and response providers in our portfolio demonstrating the importance of understanding third party risk in your ecosystem.
As businesses become more aware of these risks, they are adopting stricter vendor selection processes and enhanced monitoring. At the same time, the interconnected nature of modern operations is driving insurance companies to adjust their underwriting practices to address these evolving threats.
Ransomware remains a persistent threat
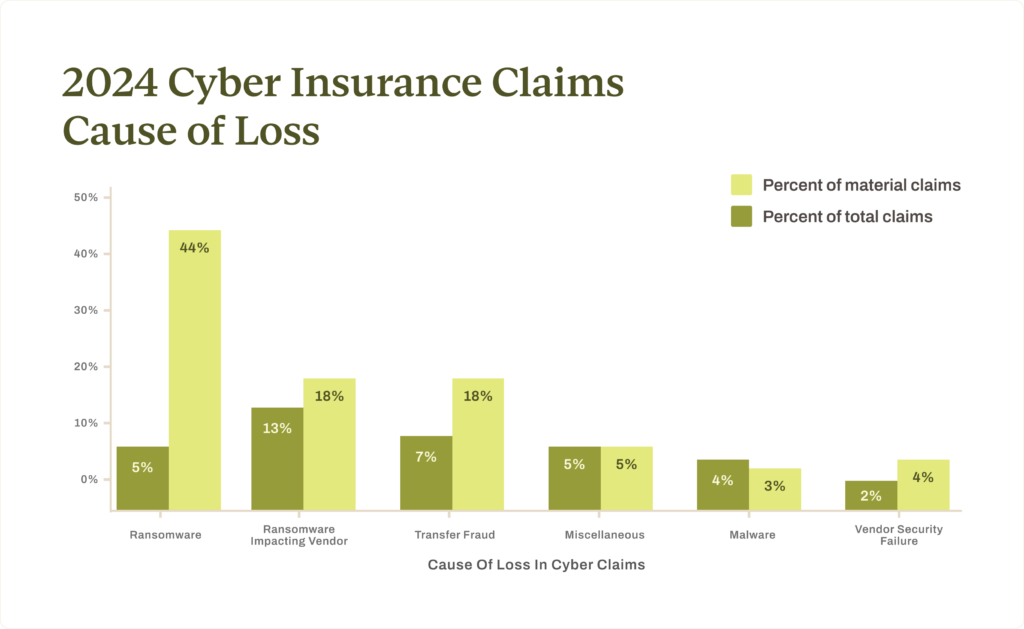
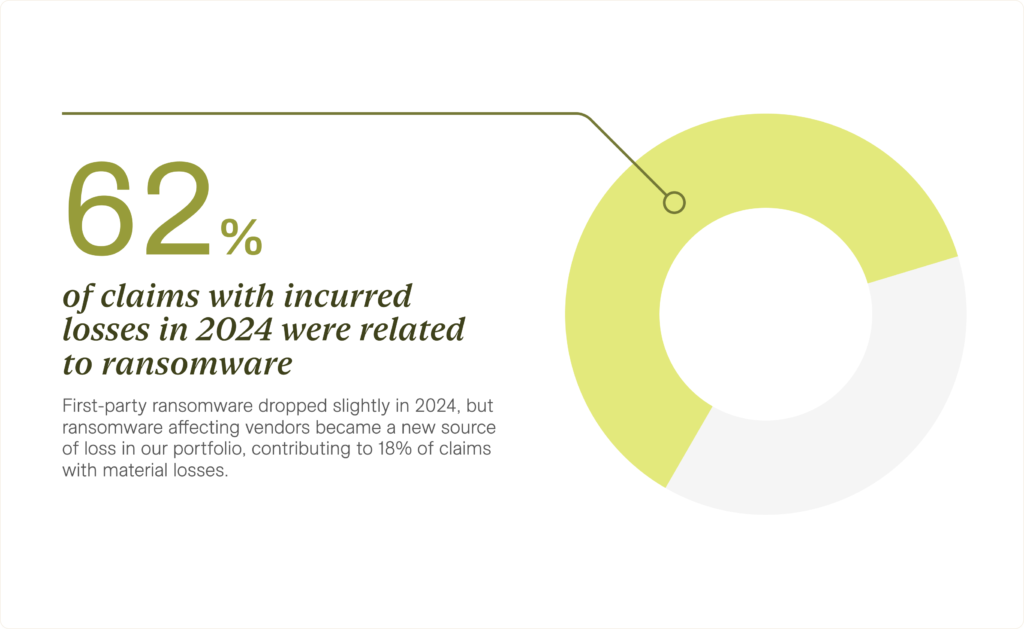
Ransomware held its position as the top cause of loss in 2024, with 43% of incurred claims involving first-party ransomware incidents. This year also saw ransomware targeting vendors emerge as a new and significant source of incurred claims, contributing to 18% of incurred claims. Altogether, 62% of claims with losses were related to ransomware.
Critical infrastructure vulnerabilities, legacy systems, and supply chain attacks were key factors driving these incidents. Industries with high-pressure environments—such as manufacturing and healthcare—were particularly vulnerable due to their reliance on (often outdated) operational technology and the high cost of downtime. Threat actors exploited these weaknesses, knowing organizations would be more likely to pay ransoms to minimize business interruptions or, in the case of healthcare, prevent the loss of human life.
While ransomware remains a significant challenge, there are indications that its frequency may be declining in broader markets. This is likely due to threat actors focusing on larger, high profile organizations that yield bigger payouts, as opposed to the previous “spray and prey” approach.
We’re also seeing greater fragmentation in the market, increased law enforcement, and a geopolitical retreat away from big, visible attacks. However, Resilience’s portfolio reflects the ongoing severity of its impact, particularly in industries with systemic vulnerabilities. The bottom line is that, while the risk of being targeted for ransomware may be reduced in comparison with years past, the impact of an organization being hit is still substantial.
An increase in transfer fraud
Transfer fraud saw a marked increase in 2024, rising from 14% of incurred claims by frequency in 2023 to 18% in 2024. Claims are not fully developed for 2024, but we expect losses from transfer fraud to exceed 2023 amounts significantly. While we can’t say precisely why this particular fraud is increasing, transfer fraud is a crime of social engineering requiring less technical skill and more manipulation tactics.
We also have evidence that the adoption of AI to build more sophisticated social engineering campaigns has allowed cybercriminals to scale attacks, resulting in increased susceptibility and higher success rates. Resilience Risk Operations Center research into the tactics of the crime group Scattered Spider suggests that crime groups are using automation to scale sophisticated attacks more rapidly.
As transfer fraud continues to grow, organizations must strengthen internal controls, educate employees on fraud prevention, and implement more robust verification processes for financial transactions. Resilience is closely monitoring this trend and adjusting underwriting strategies to address the heightened risk moving into 2025.
Shifts in points of failure
Phishing, once a primary point of failure, showed a decline in 2024, falling below vendor-related claims in frequency. This shift reflects both improvements in phishing defenses and the shift toward attacks targeting third-party vulnerabilities. In 2023, phishing was at fault in 20% of incurred claims but only 9% in 2024, a drop of 55%. Vendor-related issues surged to 27% of incurred claims in 2024 including vendor outages, ransomware affecting vendors, and vendor vulnerabilities, up from 6% in 2023.

Healthcare and finance industries drove the most total claims in the Resilience portfolio, however, when we adjust for portfolio composition, transportation and warehousing and administrative and support industries edge out manufacturing and healthcare to top the list for incurred claims. Industries like transportation, logistics, manufacturing and healthcare often rely on legacy technology or on interconnected systems that are difficult to integrate and secure. Threat actors leveraged these vulnerabilities to exert pressure, leading to higher ransom payments.
What business leaders can do next
In light of these evolving threats, CFOs, CISOs, and CROs need a proactive strategy to reduce cyber risk and build resilience. Here’s where to start:
- CFOs: Prioritize cyber risk quantification to understand potential financial exposure. Ensure adequate investment in cyber risk mitigation and explore cyber insurance policies that align with your risk profile.
- CISOs: Strengthen third-party risk management by conducting rigorous vendor assessments, implementing continuous monitoring, and requiring vendors to meet security standards. Enhance ransomware defenses with robust backup strategies, endpoint detection, and employee training.
- CROs: Align cyber risk management with enterprise risk strategies by incorporating scenario planning and stress testing for third-party breaches and ransomware incidents. Develop a clear response plan that integrates security, compliance, and insurance considerations.
The trends of 2024 have reshaped the cyber risk landscape, with third-party risks and ransomware leading the way. These challenges demand a proactive approach to risk management, one that prioritizes collaboration, vigilance, and innovation. As we move into 2025, leveraging insights from the past year will be critical for staying ahead of evolving threats and ensuring resilience in an increasingly interconnected world.








